In today's digital age, data governance has become a critical concern for individuals, organisations, and governments alike. With the ever-increasing volume and value of data being generated, transmitted, and stored, ensuring its security and privacy has become paramount. One crucial element that serves as a building block for data governance is end-to- end encryption (E2EE) technology. End-to-end encryption offers a powerful solution to protect sensitive information, foster trust, and enable secure communication across various platforms.
The basics
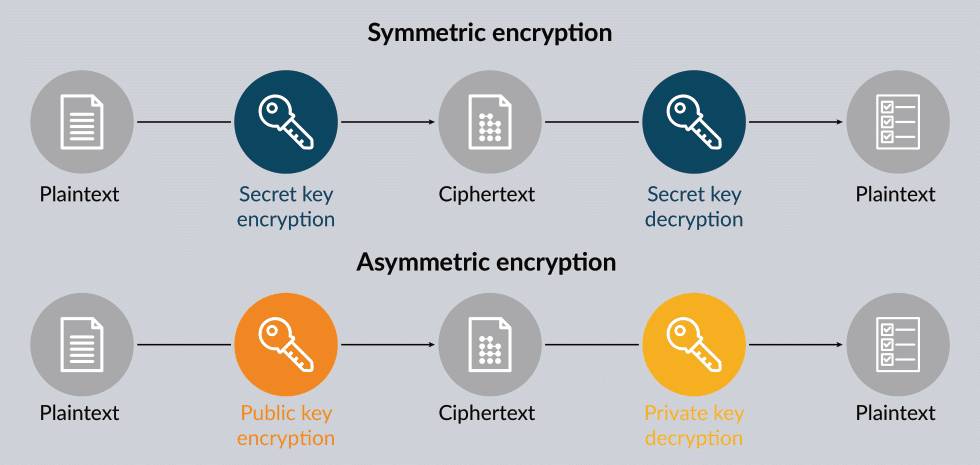
End-to-end encryption is a method of securing data in transit or at rest by encrypting it on the sender's device and decrypting it only on the recipient's device. Unlike other forms of encryption, E2EE ensures that data remains confidential and inaccessible to anyone except the intended parties involved in the communication. This includes service providers, third- party intermediaries, and even the platform administrators themselves. Only the sender and the recipient hold the cryptographic keys necessary to encrypt and decrypt the data, making it highly secure.
One of the key advantages of end- to-end encryption is its ability to safeguard sensitive information from unauthorised access and surveillance. With E2EE, even if a third-party gains access to the data during transmission or storage, they would only see encrypted, unintelligible information. The encryption algorithms used in E2EE are mathematically secure and practically unbreakable within a reasonable timeframe, ensuring that the data remains protected against potential threats.
By implementing end-to-end encryption, organisations can enhance their data governance practices in several ways. Firstly, E2EE provides a strong foundation for compliance with privacy regulations and data protection laws, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations emphasise the importance of protecting personal and sensitive information, and E2EE aligns perfectly with their requirements.
Secondly, end-to-end encryption allows organisations to demonstrate their commitment to data security and privacy, fostering trust among their customers and stakeholders. By implementing robust encryption measures, organisations can reassure their users that their data is being handled responsibly and that their privacy is being respected. Trust is a vital element in today's data-driven world, and E2EE helps build and maintain that trust.
Furthermore, end-to-end encryption can prevent data breaches and unauthorised data access. As data breaches continue to make headlines, organisations must prioritise the protection of their sensitive information. E2EE ensures that even if a breach occurs, the data stolen would be encrypted and useless to attackers. This adds an extra layer of security, minimising the potential damage caused by such incidents.
How E2EE plays out in the real world.
End-to-end encryption is used when data security is necessary, including in the finance, healthcare and communications industries. It is often used to help companies comply with data privacy and security regulations and laws.
Major service providers like Google (Gmail), Yahoo, or Microsoft hold copies to the decryption keys. This means these providers can read users’ email and files. Google has used this access to profit off of users’ private communications via targeted ads. By contrast, in well-constructed end-to-end encrypted systems, providers never have access to the decryption keys.
The simplest way to explain Gmail’s current encryption is to think about the email message traveling from the sender’s computer to the intended email recipient. During transit, digital messages are encrypted via Transport Layer Security (TLS), a protocol that provides security between the client/ server applications that communicate with each other over the internet.
The misconception comes into play when the message is at rest at the sender, intermediary servers or the recipient. At those points, the message is not encrypted. Another time the message is not encrypted is if the recipient’s email program does not accept HTTPS (using TLS) messages. Your messages are encrypted only if you and the people with whom you exchange email both use email providers that support Transport Layer Security. Not every email provider uses TLS, and if you send or receive messages from a provider that doesn't, your message could be read by eavesdroppers. While TLS isn’t a perfect solution, if everyone uses it, snooping on email will be more difficult and costly than it is today.
The privacy debate
One of the critiques of end-to-end encryption is that it allows unrestricted privacy. While end-to-end encryption is highly secure, it can also pose challenges for certain aspects of data governance, such as content moderation and law enforcement investigations. Since the data is encrypted and inaccessible to anyone except the sender and recipient, it becomes more difficult for platforms to monitor and moderate potentially harmful or illegal content.
Law enforcement, intelligence agencies, and governments tend to argue that end-to-end encryption makes it harder to keep tabs on illicit activities—such as child abuse, human trafficking, or terrorism—leading some to complain about data going dark. Since EE2E makes it impossible for providers to read the messages passing through their servers, it makes it increasingly difficult to detect the transmission of harmful content.
On the other hand, privacy advocates, human rights activists, and technologists tend to agree that people should be able to communicate online without anyone eavesdropping on their conversations, and that end-to- end encryption helps shield ordinary citizens from government overreach and mass surveillance—particularly at a time when digital communication platforms are essential for nearly everything - from organising protests to attending medical appointments.
Striking the right balance between privacy and security while addressing these concerns is crucial and requires thoughtful consideration and collaboration between technology companies, policymakers, and other stakeholders.
Section 84A of the IT Act 2000 empowers the Central Government to develop encryption standards and methods to protect electronic communications while providing e-governance and e-commerce. End-to- end encryption prevents unauthorised access to sensitive data irrespective of whether it is integrated, while in transit or at rest.
While India has now introduced traceability through the subsequent IT Rules of 2021, Brazil has modified its Criminal Procedural Laws to conform to its requirements. The United States of course has also moved in this direction by forming the 'Five Eyes Alliance' to gain access to encrypted communications.
In conclusion, end-to-end encryption serves as a crucial building block for data governance in the digital age. By employing E2EE, organisations can protect sensitive information, comply with privacy regulations, and foster trust among their users. However, it is essential to address the challenges associated with encryption while ensuring that legitimate concerns such as content moderation and law enforcement investigations are adequately addressed. Ultimately, the effective implementation of end- to-end encryption can significantly enhance data governance practices and contribute to a more secure and privacy-conscious digital ecosystem.
Aryacom and Dekkoserve enters the Indian E2EE market
Aryacom a J M Baxi group company and DekkoSecure an Australian cybersecurity software developer company have signed an exclusive partnership agreement for the Indian market. Dekko is trusted by organisations of all sizes across the globe for ultra-secure file sharing, collaboration, eSignatures, and video conferencing. The Dekko solution is set to revolutionise how government organisations and enterprises will share and collaborate on highly sensitive information. DekkoSecure is a global leader in cybersecurity solutions.
Some of DekkoSecure's global success stories
- A large financial services company was able to reduce its risk of data breaches by 90 percent after implementing DekkoSecure's solutions.
- A small business was able to recover from a ransomware attack within 24 hours after using DekkoSecure's incident response services.
- A government agency was able to improve its compliance with data protection regulation after implementing DekkoSecure's solutions.
Aryacom and DekkoSecure strives to occupy a major space in the Indian market to provide Software as a service (SaaS) solutions with military- grade security, that allows government and enterprises of all sizes to easily share and collaborate on highly sensitive and confidential information.